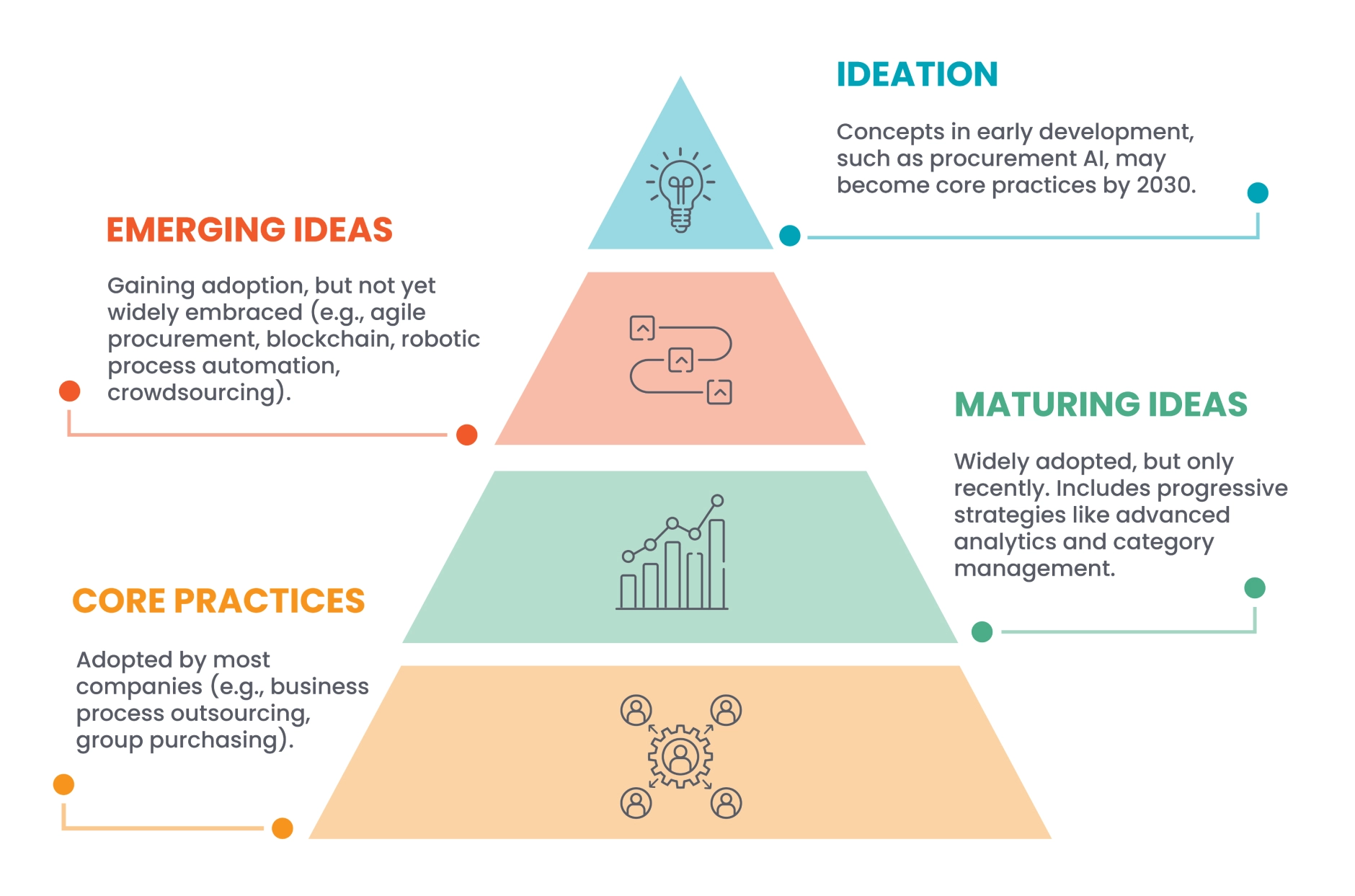
During the formation of the ‘Bold Procurement Predictions for 2030′ Insights series, ProcureAbility was keenly focused on procurement teams’ maturity levels for accepting new practices and emerging trends. It quickly became clear that procurement organizations are all over the map in terms of the new processes and technologies adopted. Some are still mired in their core practices, while a small group of innovators are ideating new ways to leverage supply chain technology. The focus of ProcureAbility’s effort was at the very top of the pyramid below: ideation.
In this Insights series, ProcureAbility explores five emerging trends that procurement organizations should anticipate will transition from the top of the pyramid to the bottom by 2030, including advanced crowdsourcing, procurement technology acceleration, cognitive computing, hyper cybersecurity, and virtual organizational design.
 In this edition of the ‘Bold Procurement Predictions for 2030’ Insights series, ProcureAbility examines a problem that has been plaguing companies for years and will only get more challenging. Digital security and the threat of data breaches are not the sole prevue of information technology professionals. Cyber-attacks frequently originate from outside the company’s firewall. Many breaches are due to inadequate protections when allowing vendors and third parties access to portions of the network.
In this edition of the ‘Bold Procurement Predictions for 2030’ Insights series, ProcureAbility examines a problem that has been plaguing companies for years and will only get more challenging. Digital security and the threat of data breaches are not the sole prevue of information technology professionals. Cyber-attacks frequently originate from outside the company’s firewall. Many breaches are due to inadequate protections when allowing vendors and third parties access to portions of the network.
That places the onus for (at least part of) data security efforts squarely on the Chief Procurement Officer.
The State of Data Security
Security experts define a cyberattack as an attempt to gain access to a computer network. The intent is almost always malicious. Cybercriminals can pursue any number of objectives: information theft, sabotage, espionage, and financial gain. Hackers are growing more sophisticated at exploiting vulnerabilities and can gain access to networks through phishing emails, malicious website access, file downloads (via the web and email), second-stage downloads, and command-and-control communications.

With businesses reporting more than 800 cyberattacks in the first half of 2022 alone, and the average long-term cost of a data breach exceeding $8.6 million, it’s not a problem that leaders can ignore.4
Sourcing for Security
The vast majority–82 percent–of technology leaders believe their supply chains are vulnerable to hackers. Procurement can expect to take on new responsibilities for the company’s data security as cybersecurity monitoring gains prominence. Evaluation (and re-evaluation) of vendors’ cybersecurity posture will become part of the sourcing process. New roles will emerge; some businesses may appoint cybersecurity category leads with duties spanning information technology and procurement.
Tighter Supplier Pools
To mitigate security risks, ProcureAbility predicts that firms will consolidate supplier pools. By 2030, many businesses will choose to work with fewer suppliers, bundling products or services. The remaining vendors will be expected to meet rigid requirements for data security. To ensure ongoing compliance, closer partnerships will evolve between sourcing, legal, and cybersecurity teams to continuously evaluate existing contracts and templates and refresh cybersecurity terms as warranted.
More Spend for Security
Across businesses of all types, investment in cybersecurity mitigation will surge as attacks become more frequent and sophisticated.
ProcureAbility predicts that cybersecurity spend will increase by 30 percent by 2030.
Finding optimal products, talent, and services in this category will be a top priority. We expect that cybersecurity monitoring and prevention services will become a top ten spend category and a crucial partnership for businesses. This will be true for large enterprises and small organizations alike. While strong cybersecurity measures have traditionally been reserved for large businesses, criminals have naturally gravitated toward smaller, less security-savvy organizations that they consider easier targets.
What Now?
Cybersecurity is an ongoing arms race between technically sophisticated criminals and the security professionals charged to protect network infrastructure. Supply chain functions, due to their close dealings with vendors and suppliers (who may not have rigorous data security standards) will find they will need to adopt new practices to protect the company. Procurement practices should expect to develop cybersecurity-related category expertise.
ProcureAbility recommends that organizations conduct detailed cybersecurity risk assessments for all vendors (either internally or through a third party), evaluate vendors’ security compliance, and develop plans to implement stringent security measures. After all, the weakest link in your data security chain could be your most trusted supplier.
Next in the ‘Bold Procurement Predictions for 2030’ Insights series: Virtual Organizational Design
Sources
1ThoughtLab, Cybersecurity Solutions for a Riskier World, 2022
2Statista, August 2022
3Upcity, May 2022
4Venafi, June 2022




